Alternate Data Stream: Hidden Files on Your PC
 This is high on the PC geek scale, but something I find that many people who consider themselves computer geeks have never heard of. I’m going to be talking briefly about Alternate Data Streams(ADS). First off, let’s discuss what it is. ADS is an undocumented feature of the NTFS file system used by Microsoft operating systems, including XP and Vista. It was added originally for compatibility to a Mac file system called HFS. Windows’ files use the file extension to determine the file type. This older Mac file system used a file within a file system to determine file type. ADS was added as a means to deal with the different processes.
This is high on the PC geek scale, but something I find that many people who consider themselves computer geeks have never heard of. I’m going to be talking briefly about Alternate Data Streams(ADS). First off, let’s discuss what it is. ADS is an undocumented feature of the NTFS file system used by Microsoft operating systems, including XP and Vista. It was added originally for compatibility to a Mac file system called HFS. Windows’ files use the file extension to determine the file type. This older Mac file system used a file within a file system to determine file type. ADS was added as a means to deal with the different processes.
Now we talk about the hidden files. Basically, what ADS does is add a file to a visible file on the file system and in doing so, hides the file. If you look at the original file in any file explorer like Windows Explorer, you see no file size change or any change except Data Modified, which does update. Note this works for any type of file, be it a text file, image file or executable file.
Here are the mechanics of how this actually works. I will give a you an example but you will need to open up your command line(Start>Run>cmd) to attempt this yourself.
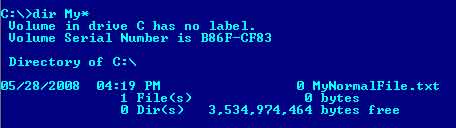
On my c drive, in my root directory, I have a file called “MyNormalFile.txt”. I also have a file called “MyHiddenFile.txt”. The first file is empty while the second one has a file size of 540 bytes. We’re going to inject “MyHiddenFile.txt” into “MyNormalFile.txt” using ADS.
At the command prompt type the below text:
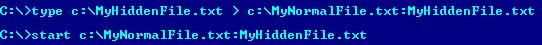
c:\> type c:\MyHiddenFile.txt > c:\MyNormalFile.txt:MyHiddenFile.txt
As long as you didn’t receive an error, the file should have injected properly. Now, if you want to run the hidden file that you just added, just type the bellow text:
c:\> start c:\MyNormalFile.txt:MyHiddenFile.txt
If I delete the original “MyHidddenFile.txt” and then run a dir, you see the following.
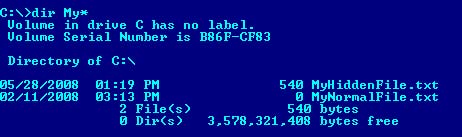
So even though both files are still there, you now only see the “MyNormalFile.txt”. It doesn’t even show the extra file space (540 bytes) of the injected file. But if you notice, it does update the modified date.
If you want to find out if you have any ADS injected files on your computer, Windows XP and older really didn’t provide a way. But you can with a freeware program from ntsecurity.nu called LNS. LNS can scan full drives and put the output into a file. With the below command, you will scan the entire c drive and put the results in a file called “lns_scan_results.txt”
c:\> lns c: > lns_scan_results.txt
When Microsoft came out with Vista, they added a switch to dir that allows you to scan for ADS like LNS. Adding the switch “/r” to the “dir” command is how you would do this.
c:\> dir /r c: > ads_scan_results.txt
I’ve had this bouncing around in my head for a couple of years, just craving for a reason to put it down to paper. I should now be able to delete that entry and make some well needed room.



No Comments Yet.